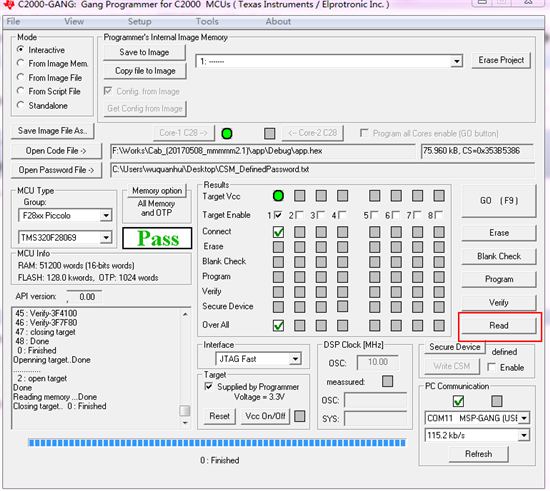
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
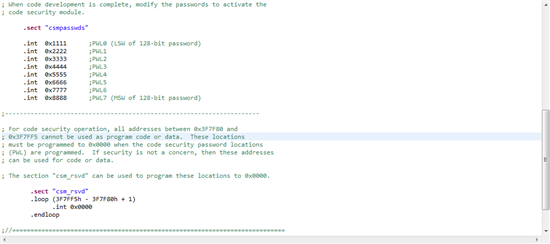
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1
Seven Han:
可以尝试debug连接下XDS仿真器,看报什么信息,确保生成加密了的.out文件。
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




user3499431:
回复 Seven Han:
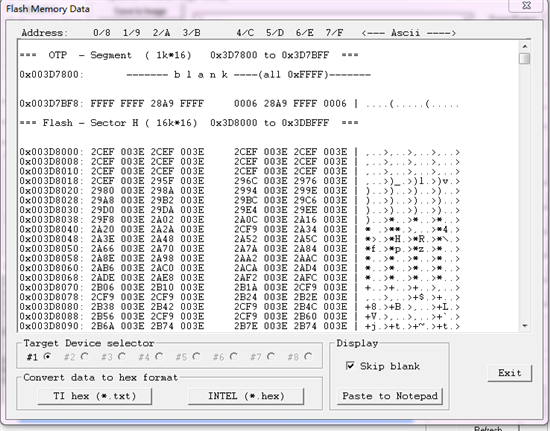
我按照你的方法试验了,发现用仿真器debug模式下烧写程序是加密成功,并且再次用仿真器debug模式,芯片已经被锁住了,如下图: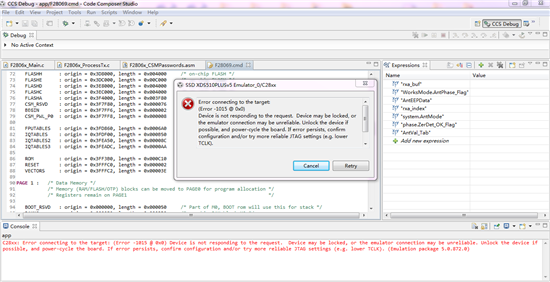
这个用debug模式烧写锁住的芯片使用C2000-GANG也是已经没办法烧写和读出程序,
但是我使用工程编译出的Hex文件,使用C2000-GANG烧写,芯片还是可以正常烧写和读出,说明
工程编译出来的Hex文件是没有被加密的,编译出来的.out文件在debug模式下烧写是加密的,
现在问题是如何设置hex文件也被加密,因为产品量产使用的C2000-GANG来烧写,并且只认识hex文件
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




Seven Han:
回复 user3499431:
请问是否尝试下hex2000工具,具体信息请查看编译器手册 http://www.ti.com.cn/cn/lit/ug/spru513n/spru513n.pdf 第12章Hex Conversion Utility Description.
这个中文说明可以参考http://blog.chinaunix.net/uid-9863638-id-3060865.html
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




user3499431:
回复 Seven Han:
我还想请教下,我用仿真器debug模式烧写,芯片加密后,再用仿真器已经无法连接芯片,用什么方法解密,我使用的是CCS5.3版本
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




Seven Han:
回复 user3499431:
可以通过外部拉低XRSN管脚,仿真器连接好后释放,通过on chip flash在弹出窗口中key0~7输入匹配PWL0~7的数值,然后Unlock。
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




JAME ORACAL:
回复 Seven Han:
我也遇到这个问题,请问还有什么别的办法么,加密之后连不上的情况有具体的文档说明吗
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




user3499431:
回复 Seven Han:
使用镊子把28069的11管脚XRSN 和GND短接,仿真器还是没办法连接,下图是 XRSN的原理连接图和连接仿真器弹出的提示:
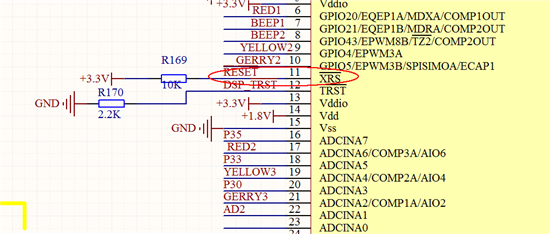
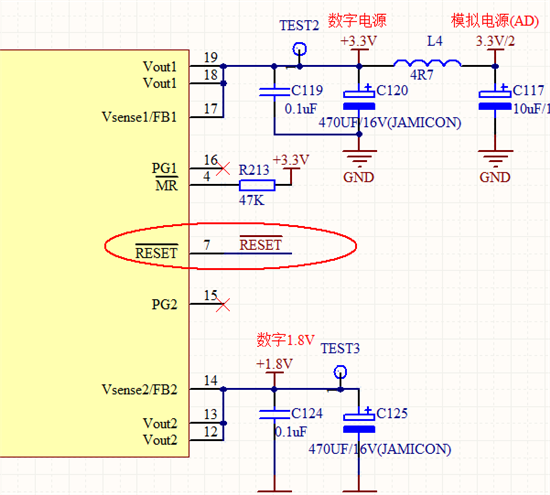
红色框是用镊子短接的管脚,但是这个管脚设计的时候连接到了电源芯片TPS70251复位管脚上,如下图:
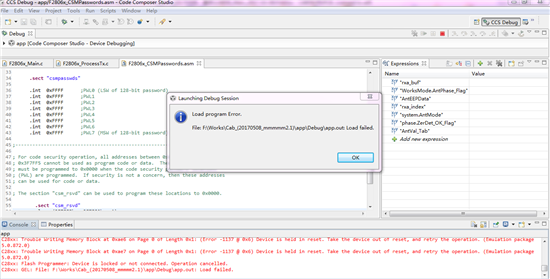
下面是仿真器连接不上的提示图:
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




user3499431:
回复 JAME ORACAL:
你是用仿真器加密的吗?
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




JAME ORACAL:
回复 user3499431:
是的啊
使用F2806x_CSMPasswords.asm文件添加到工程中,设置好密码,编译可以通过,生成的HEX文件使用C2000_GANG烧写成功,但是使用C2000_GANG界面中的读数据,可以把烧写进去的HEX文件给读出来,加密不起作用????是不在主程序中还要进行相关配置,还是CMD文件不对?
F2806x_CSMPasswords.asm中的代码如下:
.sect "csmpasswds"
.int 0x1111 ;PWL0 (LSW of 128-bit password)
.int 0x2222 ;PWL1
.int 0x3333 ;PWL2
.int 0x4444 ;PWL3
.int 0x5555 ;PWL4
.int 0x6666 ;PWL5
.int 0x7777 ;PWL6
.int 0x8888 ;PWL7 (MSW of 128-bit password)
.sect "csm_rsvd"
.loop (3F7FF5h – 3F7F80h + 1)
.int 0x0000
.endloop
CMD文件相关内容如下:
MEMORY
{
PAGE 0 : /* Program Memory */
/* Memory (RAM/FLASH/OTP) blocks can be moved to PAGE1 for data allocation */
RAML0 : origin = 0x008000, length = 0x000800 /* on-chip RAM block L0 */
RAML1 : origin = 0x008800, length = 0x000400 /* on-chip RAM block L1 */
OTP : origin = 0x3D7800, length = 0x000400 /* on-chip OTP */
FLASHH : origin = 0x3D8000, length = 0x004000 /* on-chip FLASH */
FLASHE : origin = 0x3DC000, length = 0x00C000 /* on-chip FLASH */FLASHD : origin = 0x3E8000, length = 0x004000 /* on-chip FLASH */
FLASHC : origin = 0x3EC000, length = 0x004000 /* on-chip FLASH */
FLASHA : origin = 0x3F4000, length = 0x003F80 /* on-chip FLASH */
CSM_RSVD : origin = 0x3F7F80, length = 0x000076 /* Part of FLASHA. Program with all 0x0000 when CSM is in use. */
BEGIN : origin = 0x3F7FF6, length = 0x000002 /* Part of FLASHA. Used for "boot to Flash" bootloader mode. */
CSM_PWL_P0 : origin = 0x3F7FF8, length = 0x000008 /* Part of FLASHA. CSM password locations in FLASHA */
SECTIONS
{
/* Allocate program areas: */
.cinit : > FLASHA, PAGE = 0 //初始化的变量和常量表
.pinit : > FLASHA, PAGE = 0 //全局构造器(C++) 初始化的变量和常量表
.text : > FLASHE, PAGE = 0 //可执行代码和常数
codestart : > BEGIN, PAGE = 0
ramfuncs : LOAD = FLASHD,
RUN = RAML0,
LOAD_START(_RamfuncsLoadStart),
LOAD_END(_RamfuncsLoadEnd),
RUN_START(_RamfuncsRunStart),
LOAD_SIZE(_RamfuncsLoadSize),
PAGE = 0
csmpasswds : > CSM_PWL_P0, PAGE = 0
csm_rsvd : > CSM_RSVD, PAGE = 0
/* Allocate uninitalized data sections: */
.stack : > RAMM0, PAGE = 1
.ebss : > RAML3, PAGE = 1 /*RAML3*/
.esysmem : > RAML2, PAGE = 1




user3499431:
回复 user3499431:
有知道怎么解决的吗?
 TI中文支持网
TI中文支持网



